Need Technology Help?
As a technology advisor, we partner with small firms and global enterprises helping them bring automation to their operational processes.
The multi tenant security model is how you protect customers and organizations’ data within a shared environment of your multi tenant software architecture.
The model should be properly optimized and maintained. Otherwise, you can encounter potential risks of security issues.
They can lead to data breaches, system downtime, and financial losses.
In this post, you’ll learn the key ways to mitigate risks of a non-optimized multi tenant security model featuring:
Multitenancy is a software architecture model which means a server runs a single software instance for each tenant yet serves multiple tenants.
A tenant is a logically separate customer or organization using a shared environment.
Each tenant has its own data access, permissions, privileges, and adjustments.
Tenants have shared access with predefined privileges to a specific proptech software instance they use.
This architecture model is opposite to single tenancy which means that you need to run a separate infrastructure and software instance for each tenant.
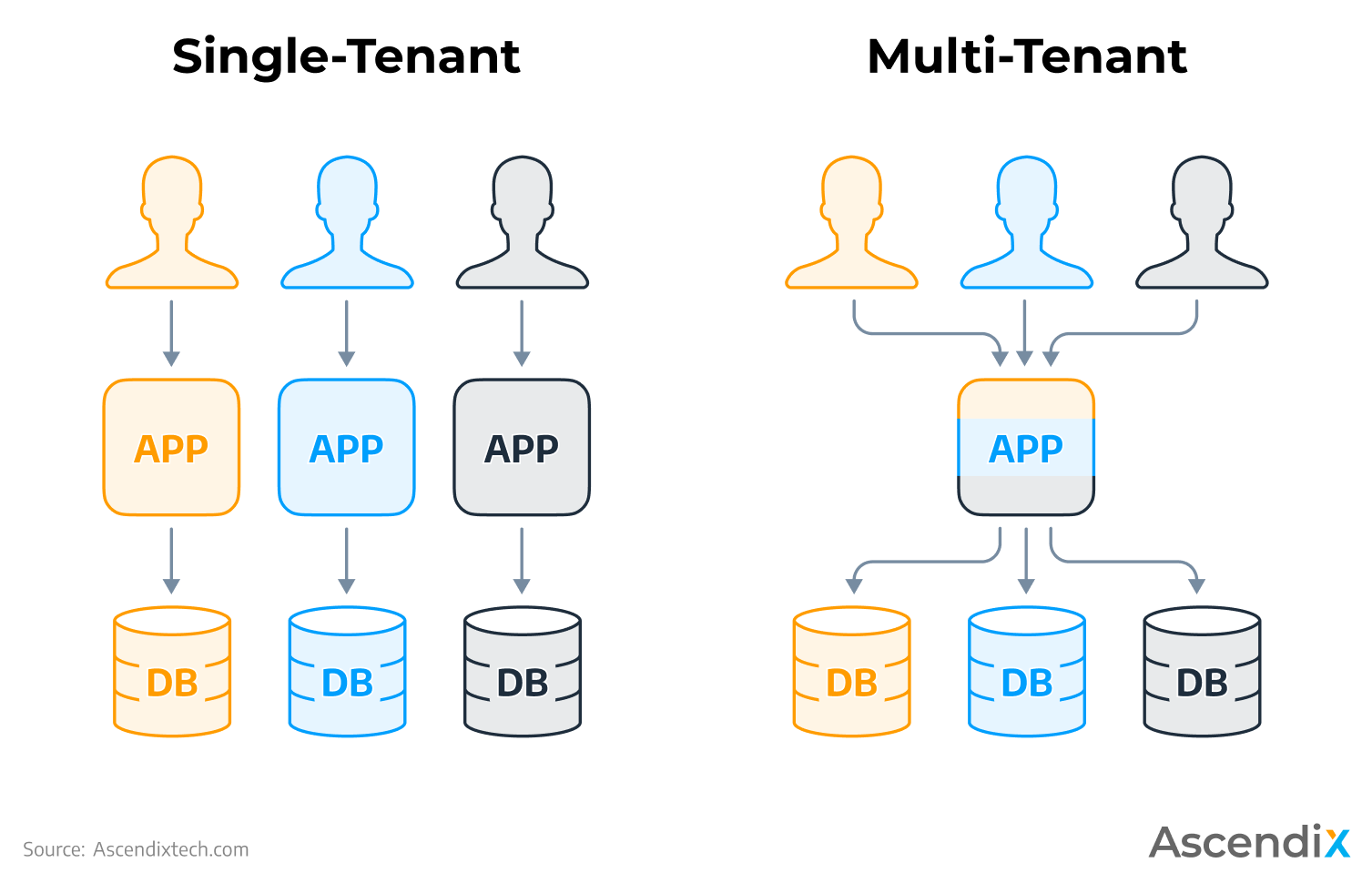
Single Tenant vs Multi Tenant | Ascendix Tech
Cloud computing often utilizes multi tenant software architecture to offer a shared environment within public cloud providers.
Google Cloud, Amazon Web Services (AWS), and Microsoft Azure are the most popular multi tenant cloud providers.
What’s more, the software-as-a-service cloud model also uses multi tenancy, so most SaaS companies deploy data within a shared approach.
As a technology advisor, we partner with small firms and global enterprises helping them bring automation to their operational processes.
The multi tenant software architecture can be categorized by the degree of layers designed to be shared across multiple tenants. The 3 key types are low, middle, and high degrees.
This type of multi tenancy means that you can share the database schema and support customized business logic, workflows, and user-interface layers.
Simply put, multi tenant software architecture is offered within all the sub-layers of SaaS software.
This type of multi tenancy in cloud computing implies that tenants are divided into small clusters that application layers and database schemas.
And each tenant cluster has its own copy of the database schema and the application instance.
In general, a middle degree means that only small SaaS clusters are multi-tenant.
This degree’s multi tenant software architecture is available for IaaS and PaaS layers providing dedicated SaaS layers for each tenant.
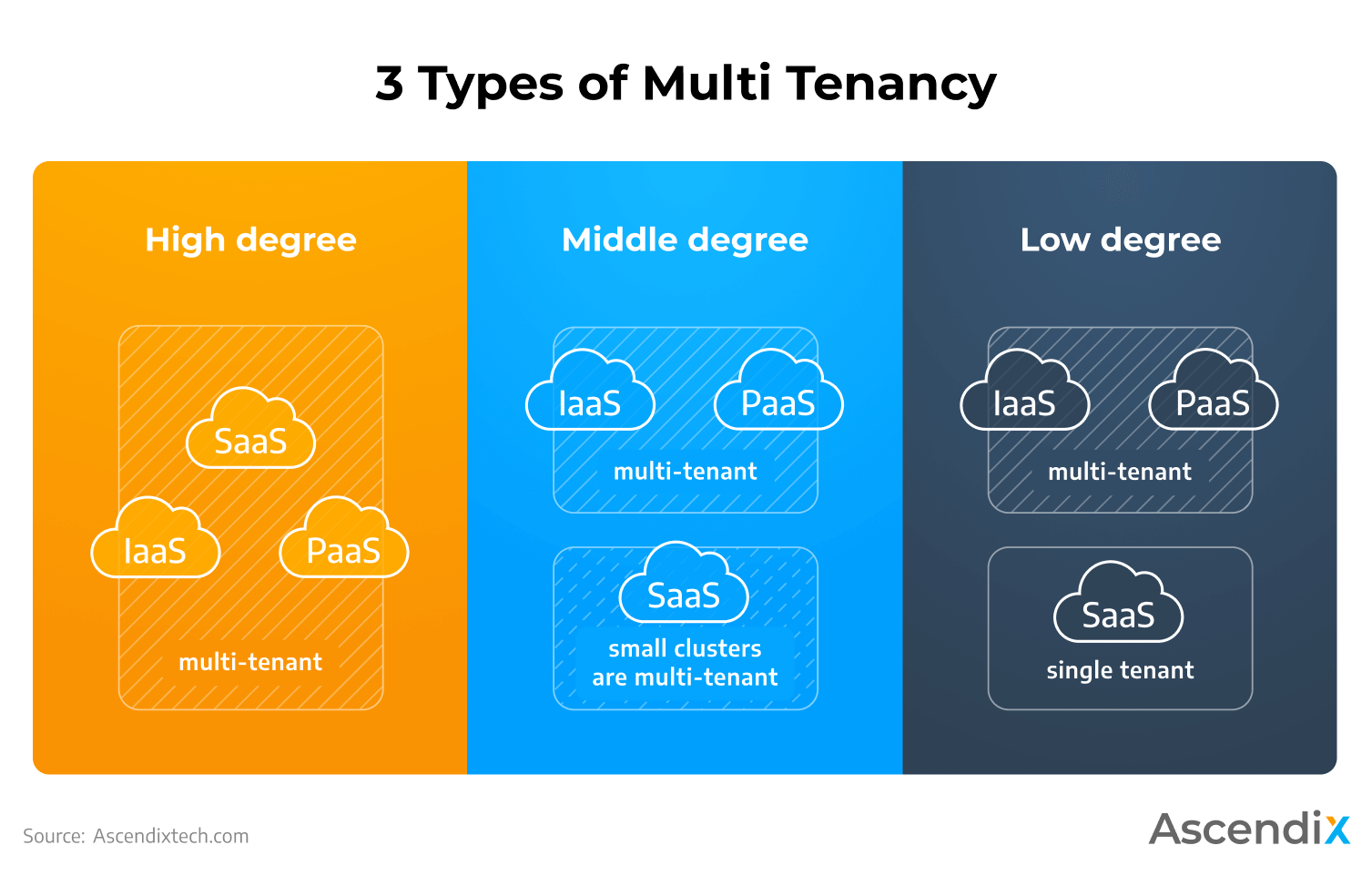
3 Types of Multi Tenancy in Cloud Computing | Ascendix Tech
For instance, Salesforce.com has over 150,000 customers supported by 16-24 multi-tenant IaaS/PaaS instances with a 1:5000 ratio.
This means that 5,000 tenants sharing the same database are supported by a single multi-tenant instance.
So, it makes Salesforce.com – a high-degree multi-tenant software provider and this is an effective model for the company as it has cross-industry utilitarian workloads.
There is no one-size-fits-all approach while choosing the multi tenant software architecture type for your system.
Carefully learn the workload needs including a strategic value, volatility, security, etc.
And keep in mind that high-degree multi tenant software architecture works best for cross-industry utilitarian workloads.
Single-tenant architecture benefits
Single-tenant architecture drawbacks
Multi-tenant architecture benefits
Multi-tenant architecture drawbacks
| Single Tenant vs Multi Tenant: Pros & Cons | |||
|---|---|---|---|
| High data security | Difficult setup and management. | Optimized bill | Low cost transparency |
| Customization opportunities | High costs | Easier deployment | |
| Faster recovery | Irrational resource usage | Efficient resource usage | |
| Portability | |||
Multi-tenancy is about public cloud deployment with a shared ecosystem utilized by multiple tenants.
This means that each user has specifically limited privileges to access a single shared database with other tenants’ data encapsulated there.
In fact, this risk is possible while utilizing a single shared database for multiple tenants.
The multi tenant software architecture leads to higher data breach risks.
In case anybody hacks into one tenant’s database, it can also influence and damage other tenants’ privacy and data within the shared environment of your Google/Azure/AWS multi tenant security model.
As we’ve stated above, one of the multi-tenant software architecture benefits is efficient resource usage.
But this advantage has a potentially critical flipside called downtime.
In case you haven’t established a highly scalable architecture, users may summarily overuse the total amount of resources you provide.
This may happen in case you supply 100Gb of memory, for example, but tenants require 120Gb.
Such overloading will often lead to a system shutdown and a costly downtime until you fix the issue within a multi tenant security model.
Multi-tenant architecture with a single shared environment for multiple tenants may lead to unexpected misconfigurations and change management risks.
If a single tenant needs configurations changes and upgrades, they may cause potential environmental glitches for other customers.
We help companies automate their workflow by developing bespoke software solutions. Leverage our experience in real estate, legal, financial, and transportation industries.
As we’ve discussed earlier, lack of isolation in multi tenant security model may potentially lead to data breaches and downtimes.
Improve your system encryption protocols and access controls in terms of cloud and virtual infrastructure.
Also, implement the approach of segmenting cloud deployments designed to enforce the application isolation to encapsulate your tenants’ data.
Data loss prevention solutions help minimize the potential risks of data breaches by monitoring the outgoing traffic of sensitive data within your application.
You can either develop your algorithms to prevent data losses or utilize ready-to-use software to prevent data leakage.
Such solutions monitor, analyze, notify, and block suspicious and unauthorized sessions to boost the data safety of your multi tenant security model.
Data sharing is also a potential security weakness of your multi tenant security model, leading to unauthorized access to sensitive data.
Implement collaboration controls that enable tracking, controlling, and detecting granular permissions of shared files.
For example, this becomes an issue when sharing data outside the organization via a web link.
Company’s employees may unwittingly share private information within their team spaces, communities, emails, and cloud storages including Dropbox, Google Drive, or Microsoft SharePoint.
The process of managing complex multiple privileges within your multi-tenant software architecture may become a potential security issue.
Lots of accounts, subscription tenancies, assets, and services permissions can lead to the overallocation of privileges across multiple accounts.
What’s more, cloud engineering and DevOps teams mostly have advanced privileges for deployment and configuration activities within a shared environment.
In case their privileges become incorrectly allocated, you may bump into a security issue.
AWS Organizations and Azure management groups are among the most effective services. They enable you to store and manage identity policies and their assignments in a centralized way.
These tools will help you ensure a proper allocation of privileges during multi-tenant deployment activities.
You should introduce governance and centralized management of permissions as a high-priority and security-oriented strategy for your tenants to keep their workflows safe.
Using and managing multiple subscriptions and accounts may lack visibility into asset configurations and inventory.
These issues lead to monitoring troubles thus providing security gaps for your multi-tenant security model.
Many cloud providers try to fix these issues by using cloud-native monitoring services.
But they are mostly isolated from accounts and don’t have enough centralization to provide a consolidated view.
What’s more, engineering teams may potentially miss some new accounts which also leads to gaps in visibility management for your AWS multi tenant security model.
Mitigate these risks by introducing cloud governance and account discovery mechanisms.
Engineering teams will follow these guidelines while developing cloud infrastructure, asset documentation, using centralized services like cloud security management.
These activities will allow you to incorporate the management and control of monitoring and configuration.
A multi-tenancy security is a way you protect customers’ and organizations’ data within a shared environment database. It has 3 types: high, medium, and low that depend on the sub-layers that support multi tenant architecture.
The three multi-tenancy models are low, middle, and high degrees. They are categorized by the degree of layers designed to be shared across multiple tenants. For example, Salesforce.com is a high-degree multi-tenant software provider because this multi-tenancy model best fits cross-industry utilitarian workloads.
Multitenancy is a software architecture model which means a server runs a single software instance for each tenant yet serves multiple tenants. Google Cloud, Amazon Web Services (AWS), and Microsoft Azure are the most popular multi tenant cloud providers.
Daniil specializes in content marketing and has a deep knowledge of promoting the company's products and services through high-quality content. On the Ascendix blog, Daniil shares his tricks and tips on custom software development, provides technology trends and insights, and helps you get valuable content to make your business even more successful and profitable.
Get our fresh posts and news about Ascendix Tech right to your inbox.